From a User Flaw to Complete God Mode¶
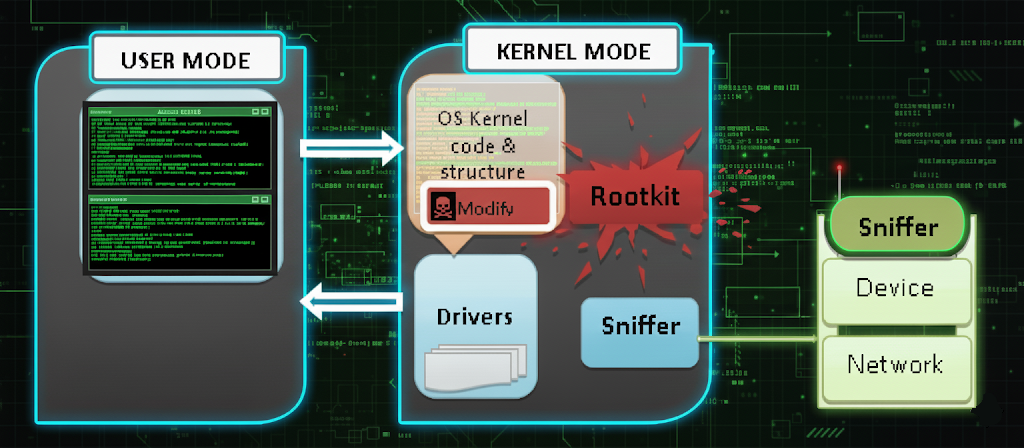
In modern operating systems, security is built upon a fundamental architectural principle: the separation of privilege levels. This model segregates the system into two primary domains: the low-privilege User-Space (Ring 3), where applications run, and the high-privilege Kernel-Space (Ring 0), which exercises complete control over the system. For a threat actor, the ultimate goal is to cross the critical boundary between these two domains.
This blog post provides a technical analysis of this process. We will explore how an initial compromise of a single application in user-space can be leveraged to attack the operating system kernel, leading to a full system takeover known as Privilege Escalation.
Part 1: The Two Execution Contexts of an OS¶
An operating system enforces a strict separation between user applications and the core of the OS, the kernel. This is not just a software convention but a hardware-enforced boundary using CPU privilege levels.
User-Space (The Restricted Environment - Ring 3) User-space is the sandboxed, low-privilege environment where all user-facing applications—browsers, office suites, games—run. Its core characteristics are its limitations: processes are isolated from one another, have no direct access to physical hardware, and are policed by the kernel. An application crash is contained and will not affect the operating system's stability.
The common types of User-Space vulnerabilities that provide an initial entry point for attackers include:
- Memory Corruption: Vulnerabilities like Buffer Overflows (Stack & Heap) or Use-After-Free, which often lead to arbitrary code execution within the context of the compromised application.
- Application Logic Flaws: A broad category including SQL Injection, Remote Code Execution (RCE) in web apps, and other similar flaws.
An exploit targeting user-space gives an attacker a foothold, but their power is confined to that single process and the permissions of the user who ran it. They have an initial presence, but they do not control the system.
Kernel-Space (The Privileged Core - Ring 0) Kernel-space is the core of the OS, the "brain stem" that runs with the highest privilege level (Ring 0). It possesses immense power: it manages memory, schedules all processes, and has direct, unrestricted access to all system hardware. This is effectively "God Mode." A vulnerability here doesn't just crash an app; it crashes the entire system, resulting in a Kernel Panic on Linux/macOS or a Blue Screen of Death (BSOD) on Windows. The kernel is the ultimate target for any serious attacker because compromising it provides complete and persistent control over the entire machine.
Part 2: The Escalation Ladder: From User to Root, and Root to Kernel¶
It's a common misconception that escalating privileges immediately requires a sophisticated kernel exploit. In reality, it is often a multi-stage process. An attacker's first goal is typically to escalate their privileges within user-space to gain administrative control. Only then might they target the kernel for ultimate stealth and persistence.
Phase 1: Privilege Escalation within User-Space (User -> Root/Administrator)¶
Before attempting to attack the highly-fortified kernel, an attacker will first seek out lower-hanging fruit within the user-space environment. The goal here is to escalate from a low-privilege account (like a web server's www-data user) to the all-powerful root or Administrator user. This can be achieved without a kernel exploit by abusing flaws in the system's configuration and the software it runs.
Common vectors for user-space privilege escalation include:
- Misconfigured Services and Weak File Permissions: Finding a service running with
rootprivileges that is improperly configured, or discovering world-writable scripts that are later executed by the administrator. - Vulnerable SUID/GUID Binaries (Linux): A SUID binary is a program that executes with the permissions of its owner, not the user who runs it. Exploiting a vulnerable application that is owned by
rootand has the SUID bit set grants an attacker a shell as therootuser. - Password Hunting: Searching for plaintext passwords or reusable password hashes in configuration files, scripts, and shell history.
At the end of this phase, the attacker has achieved a major objective: they have a shell running with root or Administrator privileges. However, it's critical to understand that they are still operating in User-Space (Ring 3). They can install software and manage the system, but their actions are still visible to the kernel and to advanced security tools.
Phase 2: The Leap from Root to Kernel-Space (Ring 0)¶
With administrative control secured, why would an attacker risk destabilizing the system by attacking the kernel? The reasons are stealth, persistence, and the ability to bypass the most advanced security defenses.
- Stealth (Rootkits): A process running as
rootis still just a process. It can be seen in the process list and its network connections can be monitored. To become truly invisible, an attacker must move into kernel-space. By loading a malicious driver or module (a rootkit), they can hook fundamental kernel functions to filter the output of system utilities, effectively erasing their processes, files, and network connections from view. - Persistence: A user-space backdoor can be found and removed. A kernel-level rootkit is far more difficult to detect and eradicate.
- Bypassing Security Software: Modern Endpoint Detection and Response (EDR) and antivirus solutions are deeply integrated into the OS, often with their own kernel drivers. To disable or blind these tools, an attacker must operate at the same privilege level—Ring 0.
This is the point where the attacker leverages their administrative access to attack the kernel itself, often by exploiting System Calls or loading a vulnerable third-party driver (BYOVD).
Part 3: Case Study - The Stuxnet Attack Chain¶
Stuxnet was not a simple piece of malware; it was a multi-stage cyber-weapon armed with an unprecedented number of zero-day vulnerabilities. Its attack chain was a sophisticated, multi-pronged operation designed for propagation, privilege escalation, and ultimate sabotage. A simplified view does not do it justice. Here is a more accurate, phased breakdown of its attack.
Phase 1: Propagation and Initial Infection (The Multi-Vector Approach)¶
Stuxnet’s primary genius was its ability to spread. It used multiple vectors to ensure it could both breach air-gapped networks and propagate rapidly within a connected environment.
-
USB Drive Vector (The Air-Gap Bridge): This was its most famous vector. The initial infection began when an operator inserted a compromised USB drive into a system. Stuxnet exploited the .LNK Vulnerability (CVE-2010-2568). The moment Windows Explorer tried to render the icon for a malicious shortcut file, it triggered a flaw in a kernel driver (
win32k.sys), immediately granting the malware kernel-level code execution. This was the key to jumping into secure, isolated networks. -
Network Worm Propagation (Spreading Internally): Once inside a local network, Stuxnet activated its worm-like capabilities to spread to other computers. For this, it used another powerful zero-day: the Windows Print Spooler Vulnerability (CVE-2010-2729). By sending a specially crafted print request to a remote computer with a shared printer, Stuxnet could execute code on that machine without any user interaction. It also utilized older but still effective vulnerabilities like the one exploited by the Conficker worm (MS08-067) to maximize its spread.
Phase 2: Privilege Escalation (Ensuring Absolute Control)¶
Gaining initial code execution was not always enough; Stuxnet needed to ensure it could operate with the highest possible privileges (NT AUTHORITY\SYSTEM) on every machine it infected. To guarantee this, it carried payloads for two different zero-day privilege escalation vulnerabilities:
- The malware would check the system's patch level. If it found itself running as a standard user, it would exploit one of these local vulnerabilities (e.g., CVE-2010-2743 in the Windows Task Scheduler) to elevate its privileges to SYSTEM. Having two separate zero-day exploits for this purpose provided redundancy and ensured its success across a wider range of target configurations.
Phase 3: Persistence and Stealth (Becoming an Invisible Rootkit)¶
With guaranteed SYSTEM privileges, Stuxnet’s next step was to embed itself deeply into the operating system and hide its presence.
- Abusing Trust with Stolen Certificates: To load its own malicious drivers (
mrkstub.sysandmrxcls.sys) and become a rootkit, Stuxnet had to bypass Windows Driver Signature Enforcement. It did this by signing its drivers with stolen private digital certificates from two highly reputable hardware companies, Realtek and JMicron. Because the drivers appeared to be from a trusted source, the Windows kernel loaded them without any security warnings. - Rootkit Functionality: Once loaded, these drivers hooked low-level system functions to hide Stuxnet's files and processes from both the user and any security software on the machine, making it extremely difficult to detect.
Phase 4: The Final Payload (The Industrial Sabotage)¶
Stuxnet’s complex propagation and stealth mechanisms all served a single, highly specific purpose.
- Target Identification: The rootkit would lie dormant, monitoring the system for the presence of Siemens' Step7 software, which is used to program and manage Programmable Logic Controllers (PLCs).
- PLC Code Injection: Upon finding a target, Stuxnet would use its kernel-level access to inject malicious code into the legitimate Siemens software. This code would then alter the logic on the PLCs controlling Iran's nuclear centrifuges. It subtly changed the rotational speeds of the centrifuges—speeding them up and slowing them down—to cause physical stress and damage, all while replaying normal operational data to the monitoring engineers, so that everything appeared to be functioning correctly.
Conclusion: Lessons from the Digital Battlefield¶
Stuxnet was more than just a piece of malware; it was a paradigm shift. It demonstrated, in undeniable terms, that the journey from a simple user-space flaw to the absolute control of kernel-space was not a theoretical exercise for security researchers, but a practical and devastatingly effective strategy employed by nation-states. The attack chain, armed with an arsenal of zero-day vulnerabilities, proved that a single infected USB drive could culminate in real-world, physical destruction. This serves as the ultimate case study for why kernel security is paramount.
The legacy of Stuxnet and similar advanced threats provides several critical lessons for any security professional or system architect:
- The Myth of the Single Exploit is Dead: Sophisticated attacks are not monolithic. They are campaigns. Stuxnet masterfully chained together vulnerabilities for propagation, privilege escalation, and persistence. Defending against one vector is not enough.
- Trust is a Weapon: The use of stolen digital certificates from Realtek and JMicron was a watershed moment. It proved that an attacker doesn't always need to break a security mechanism if they can steal the keys to unlock it. The supply chain and the integrity of trusted third parties are now critical components of system security.
- The Kernel is the Ultimate Goal: While initial access is noisy and often occurs in user-space, the true objective for a persistent adversary is Ring 0. Gaining kernel-level execution allows an attacker to become part of the operating system's trusted computing base, rendering them invisible and granting them total control.
Building a Resilient Defense¶
Understanding this attack path from user flaw to "God Mode" allows us to formulate a more robust defensive strategy. Protection cannot be a single layer but a deep, overlapping series of controls:
- Aggressive Patch Management: Stuxnet's success relied on unpatched systems. A rigorous patching policy for both user-space applications (browsers, office suites) and the operating system kernel is the most fundamental and effective defense.
- Enforce the Principle of Least Privilege (PoLP): An attacker who compromises a standard user account has a much harder journey than one who lands on an account with administrative rights. Limit user permissions to the absolute minimum required.
- Kernel Integrity and Hardening: Modern security features are designed to prevent Stuxnet-like attacks. Secure Boot ensures that the kernel itself hasn't been tampered with, while Driver Signature Enforcement (on Windows) and signed module enforcement (on Linux) are critical for preventing the loading of unauthorized kernel code.
- Network Segmentation: Stuxnet's worm-like capabilities were devastating. Segmenting networks to limit lateral movement can contain a breach and prevent a single compromised machine from infecting an entire organization.
While Stuxnet was discovered over a decade ago, the techniques it pioneered continue to evolve. The concept of abusing trust is now seen in modern "Bring Your Own Vulnerable Driver" (BYOVD) attacks used by ransomware groups. The boundary between user-space and kernel-space remains the most critical battleground in cybersecurity. Defending it requires constant vigilance, a defense-in-depth mindset, and a deep understanding of the sophisticated adversaries who seek to cross it.